![Cisco Secure Firewall Threat Defense Virtual Getting Started Guide, Version 7.2 and Earlier - Deploy the Threat Defense Virtual on VMware [Cisco Secure Firewall Threat Defense Virtual] - Cisco Cisco Secure Firewall Threat Defense Virtual Getting Started Guide, Version 7.2 and Earlier - Deploy the Threat Defense Virtual on VMware [Cisco Secure Firewall Threat Defense Virtual] - Cisco](https://www.cisco.com/content/dam/en/us/td/i/400001-500000/460001-470000/466001-467000/466189.jpg)
Cisco Secure Firewall Threat Defense Virtual Getting Started Guide, Version 7.2 and Earlier - Deploy the Threat Defense Virtual on VMware [Cisco Secure Firewall Threat Defense Virtual] - Cisco
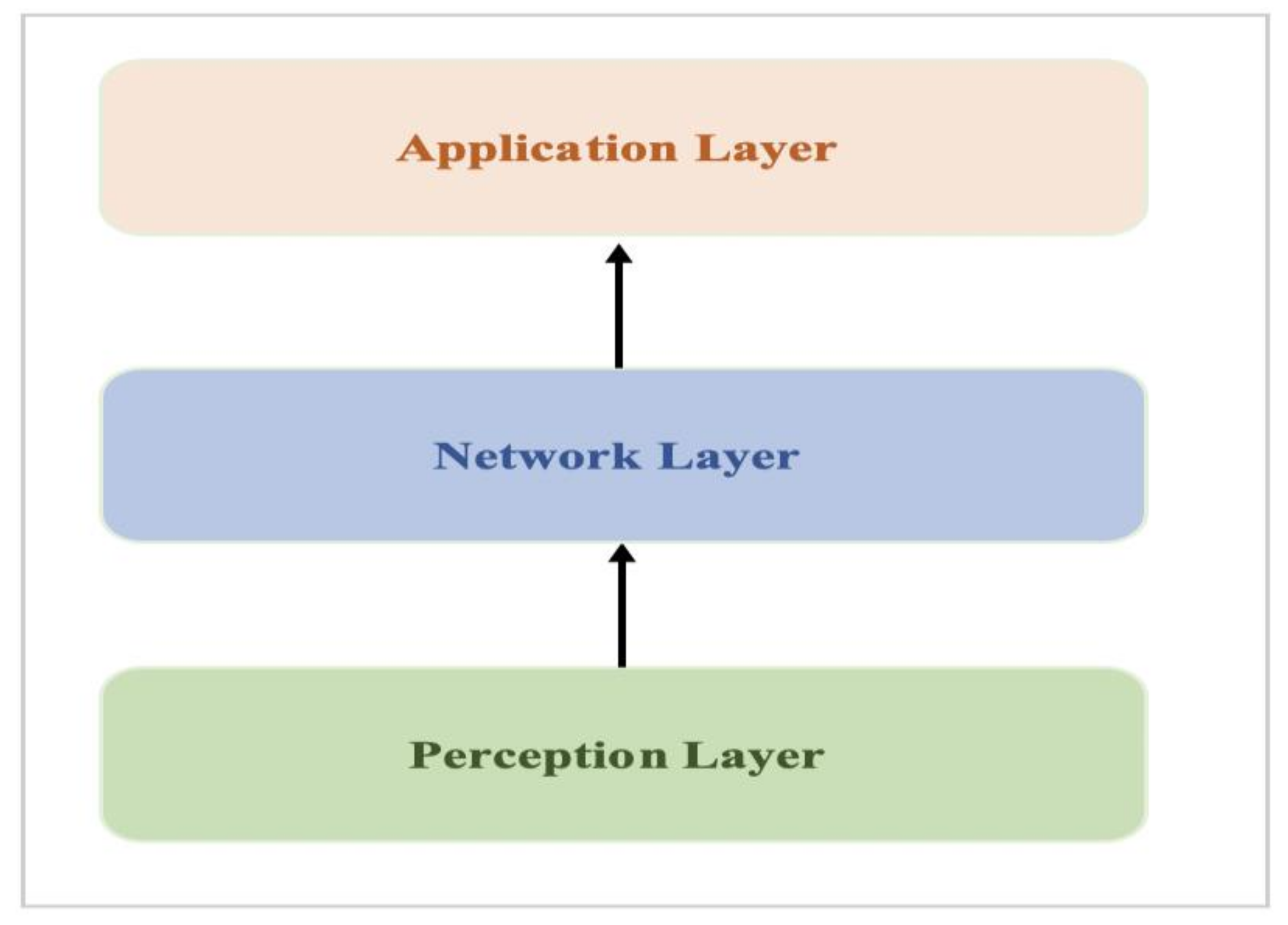
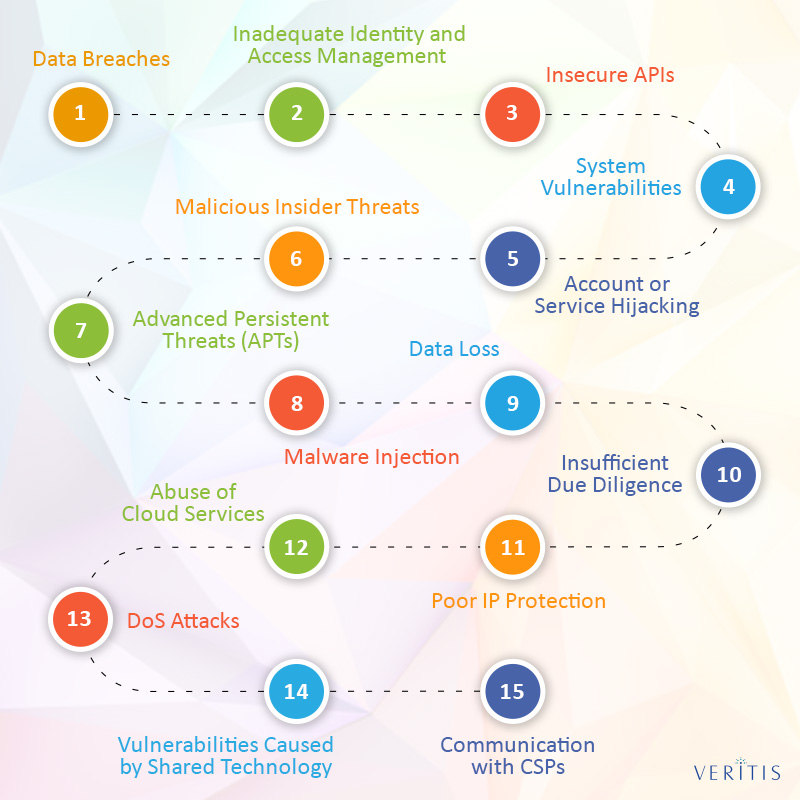
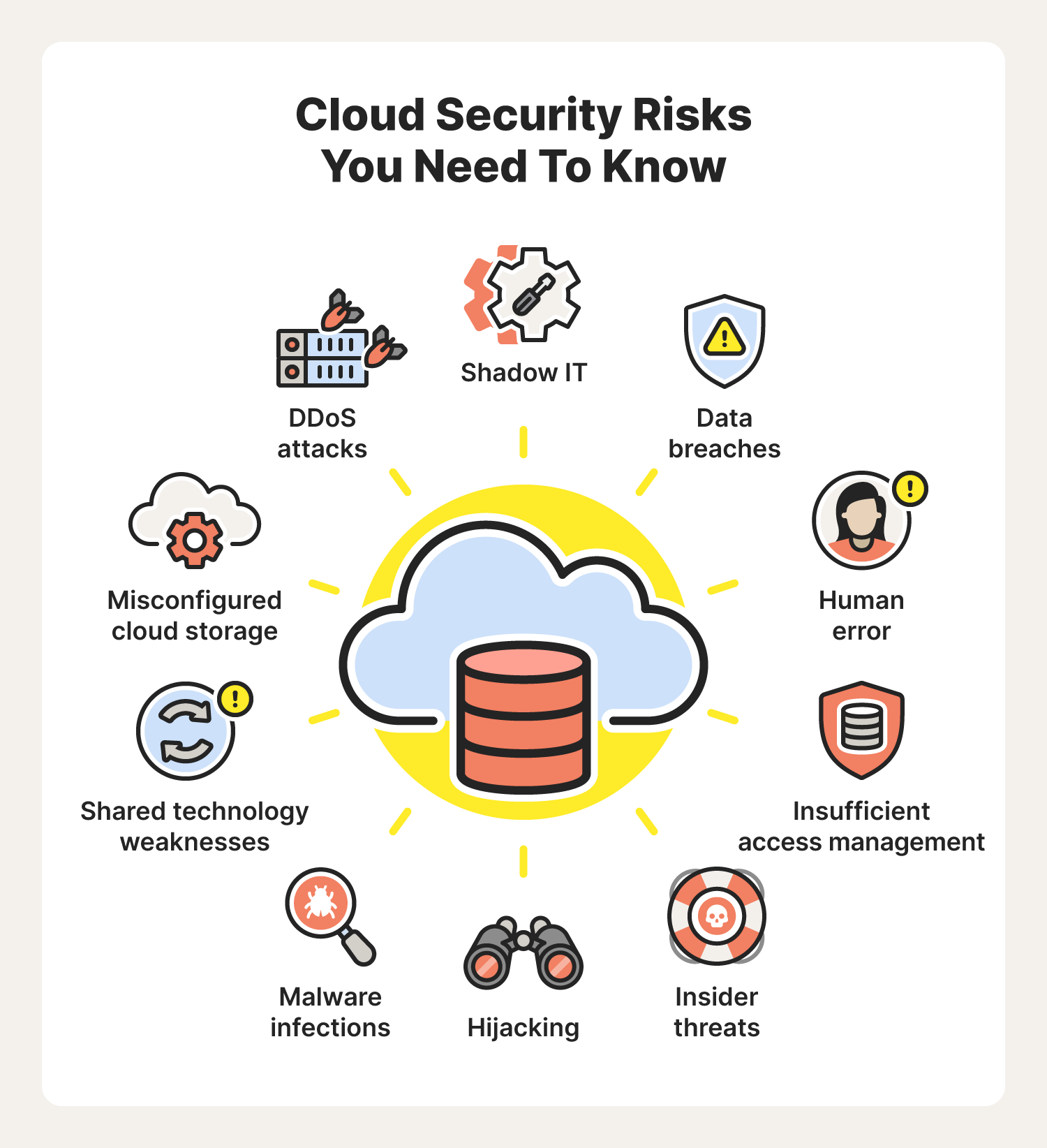
Electronics | Free Full-Text | Cybersecurity Threats, Countermeasures and Mitigation Techniques on the IoT: Future Research Directions
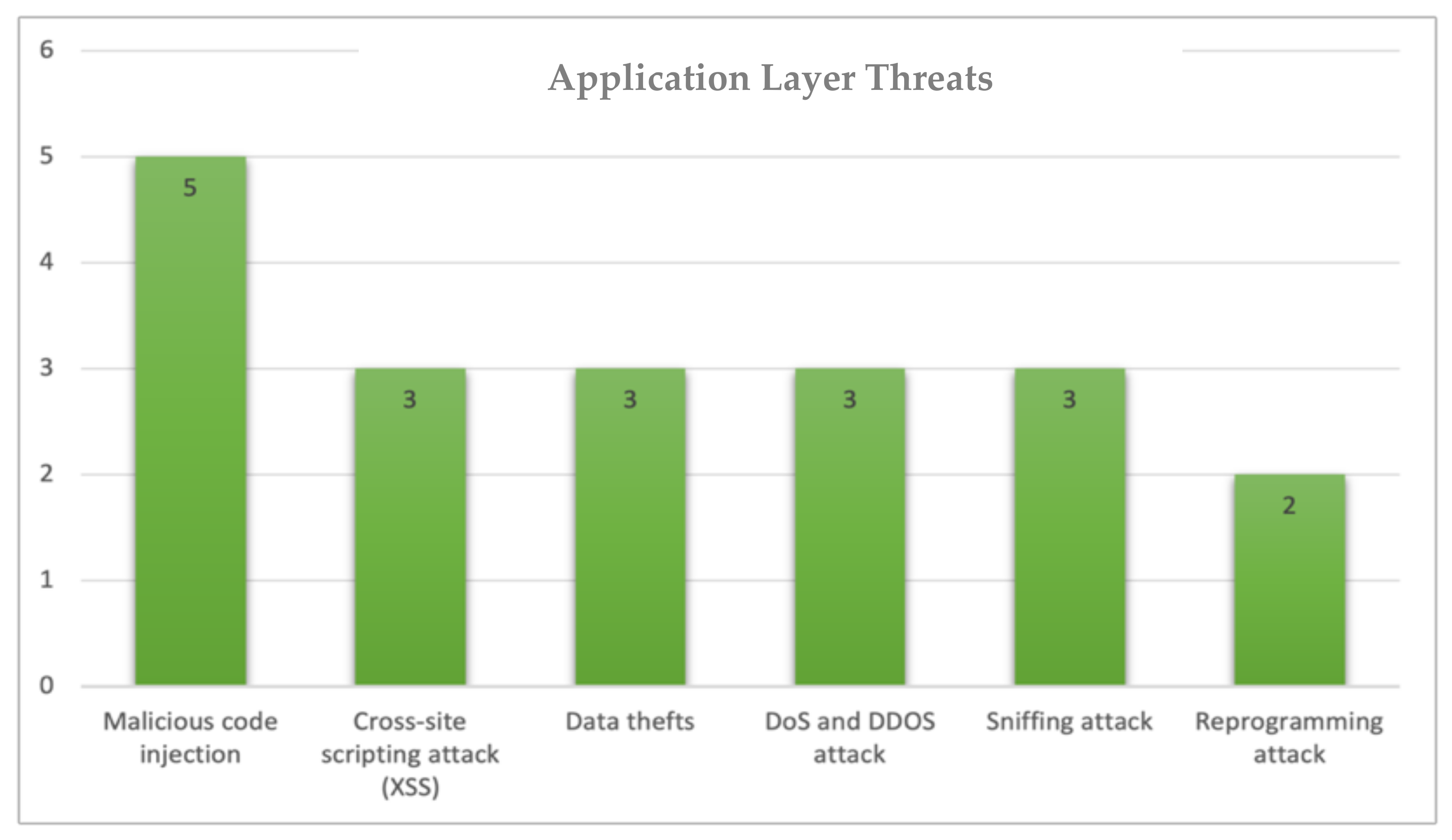
Electronics | Free Full-Text | Cybersecurity Threats, Countermeasures and Mitigation Techniques on the IoT: Future Research Directions

Risk vs Threat: The Fatal Mistake You're Making in Your Security Strategies | by CyberSec_Sai | InfoSec Write-ups
![Cisco Secure Firewall Threat Defense Virtual Getting Started Guide, Version 7.2 and Earlier - Deploy the Threat Defense Virtual on VMware [Cisco Secure Firewall Threat Defense Virtual] - Cisco Cisco Secure Firewall Threat Defense Virtual Getting Started Guide, Version 7.2 and Earlier - Deploy the Threat Defense Virtual on VMware [Cisco Secure Firewall Threat Defense Virtual] - Cisco](https://www.cisco.com/content/dam/en/us/td/i/400001-500000/460001-470000/466001-467000/466188.jpg)